The 10 most common social engineering attacks to look out for: Have you ever fallen victim to these “Human Hacking” scams?
The more we learn about how to keep our computers secure, the more we realize that people are the weakest link of defense in the chain. Everyone, even those who fall for scams, however, often think they are too savvy to be taken in. Hackers, con artists, and thieves have a potent arsenal of social engineering tactics to breach your defenses and steal sensitive information. Understanding their tactics can help you avoid falling into their trap.

What is social engineering?
Social engineering is the art of manipulating, influencing, or deceiving unsuspecting users into exposing data, spreading malware infections, or giving access to restricted systems. The hacker might use the phone, email, snail mail, or direct contact to gain illegal access.
Unlike computer hacking where an attacker exploits weaknesses in software design, social engineering involves the exploitation of human vulnerabilities. Social engineers target irrational behavior, cognitive biases, distractedness, and emotions.
How do social engineering attacks work?
Steps for the social engineering attack cycle are usually as follows:
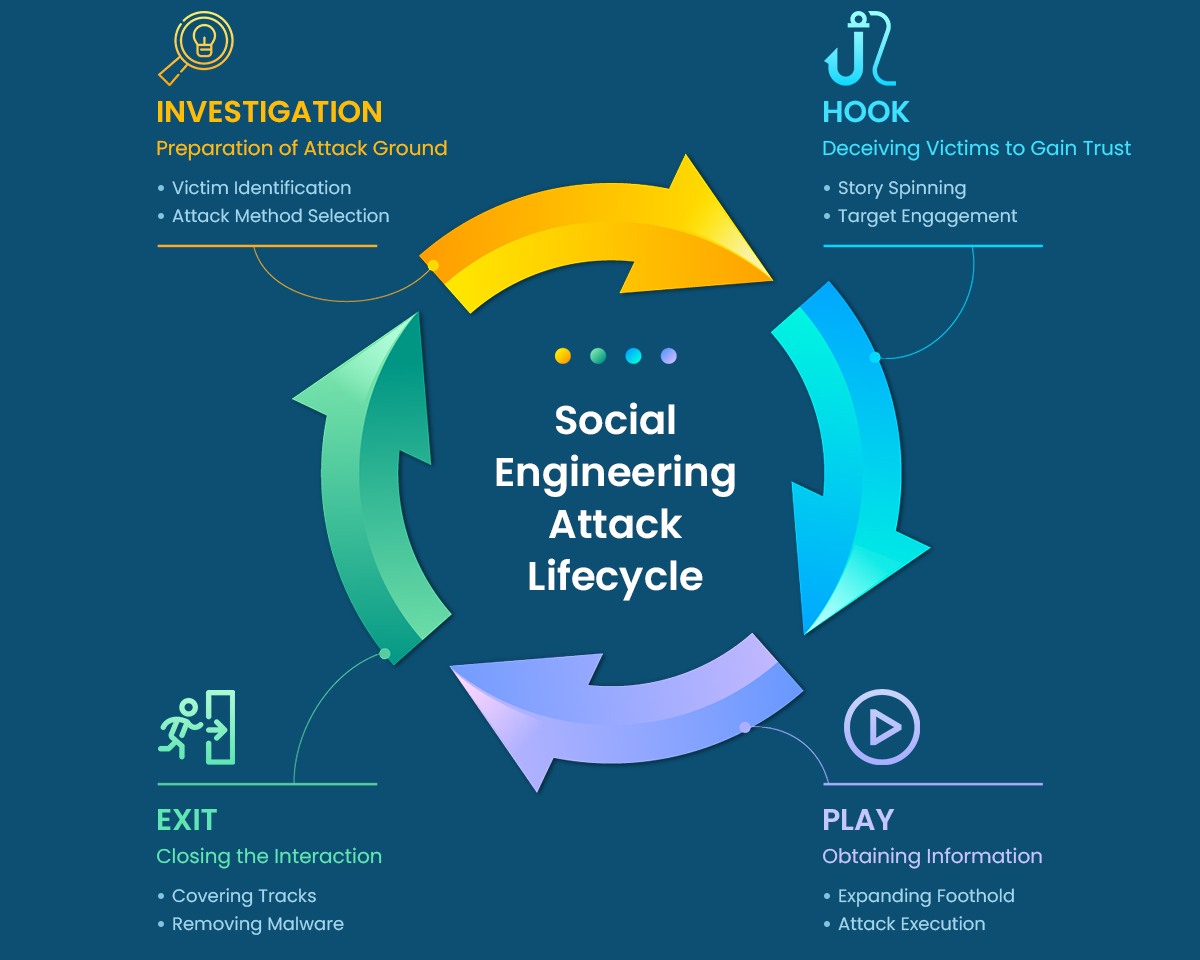
Types of social engineering attacks
1. Phishing

Phishing is the most prevalent and common type of social engineering attack. This kind of scam comes in various flavors, including email, phone calls, social media posts, text messages, or website that has been intended to fake trustworthy systems and organizations. Phishing attacks encapsulate social engineering tactics, creating a sense of curiosity, fear, or urgency to coerce victims into visiting suspicious websites and divulging sensitive information, such as passwords and credit card details.
A social engineer might pose as a banking institution, for instance, asking email recipients to click on a link to log in to their accounts. Those who click on the link, though, are taken to a fake website that, like the email, appears to be legitimate. If they log in at that fake site, they’re essentially handing over their login credentials and giving the cybercriminal access to their bank accounts.
Most phishing attacks have the following characteristics:
- email appears to come from a trustworthy source such as your bank, cable TV provider, or tech support.
- aims to obtain personal data such as addresses and social security numbers
- main goal is to steal identity or money
- link shorteners such as bit.ly to conceal fake websites
- suspicious URLs (wrong spelling, strange punctuation marks, inaccurate domain extensions, etc.) that lead to fake websites
- has warnings, emergencies, or cash prizes to manipulate the target’s emotions
- may use attachments with malware
2. Smishing/SMS-phishing

SMS-phishing, or smishing, is a social engineering attack conducted specifically through SMS messages. SMS phishing or SMiShing, is a type of phone text message used by cybercriminals to collect valuable information, request fund transfers or gift cards, and even distribute malware. These text messages lure recipients into responding because they often appear to be a message from an executive manager within an organization.
Smishing attacks have increased in popularity amongst criminals as people spend more time on mobile devices. While users have become savvier at detecting email phishing, many people are far less aware of the risks associated with text messages.
A smishing attack requires little effort for threat actors and is often carried out by simply purchasing a spoofed number and setting up the malicious link.
3. Vishing

Vishing (short for voice + phishing), also known as voice phishing, is another form of Smishing, but this phone-based attack uses voice calls/messaging. Vishing attackers use voice-changing software to obscure the caller’s identity and convince or urge victims they must act quickly to protect themselves from arrest or other risks. The messages sometimes also promise gifts or services in exchange for payment. Banks, government agencies, and law enforcement agencies are commonly impersonated personas in vishing scams. The goal is to gather victims’ personal information, credit card numbers, or credentials.
Vishing scams like this one often target older individuals, but anyone can fall for a vishing scam if they are not adequately trained.
4. Pretexting

Pretexting is a more sophisticated style of social engineering attack when a scammer creates a fabricated scenario that sounds trustworthy in order to gain the victim's trust and trick victims into revealing sensitive information such as passwords, financial information, or social security information. While phishing often relies on fear and urgency, pretexting leverages trusted relationships with victims. Pretexting is highly effective as it reduces human defenses to phishing by creating the expectation that something is legitimate and safe to interact with.
The attacker usually starts by establishing trust with their victim by impersonating co-workers, police, bank and tax officials, or other persons who have right-to-know authority. After explaining the context, the attacker would then ask the victim questions to gain personal and sensitive information, which they could then use to advance other attack scenarios or access their personal accounts.
5. Catfishing

Catfishing is when scammers create fake social media profiles by using other people’s photos, videos, and personal information to lure them into a relationship with a false identity. These fake identities are typically used to cyberbully or seek attention. Sometimes, they can also be used to extract money or the victim’s personal details.
If you’ve made an online friend who is extremely nice but constantly finds excuses to not meet in person or to share information about themselves, it’s very likely that you’re being catfished. Here are some warning signs:
- Pity stories and requests to donate money
- Strange excuses such as why their webcam or phone doesn’t work
- Excuses not to meet up or last-minute cancellations due to personal emergencies
- Offering to meet somewhere private rather than in a public place
6. Scareware

If you ever saw a pop-up on your screen saying something like “Warning! Virus Alert!” or “Warning! 5 Virus Detected!”, that’s scareware in action. While previously discussed social engineering techniques rely on trust, lack of awareness or knowledge, or greed, scareware relies on a user's fear to trick them. Scareware typically takes the form of malicious software or pop-ups that attempt to scare you into visiting and downloading more malicious materials.
Social engineers inundate you with false alerts, made-up threats, and “urgent” warnings to create panic in users’ minds. Pop-ups that try to get you to click on them, claiming that your computer is infected with malicious files or pornography are common scareware tactics. It aims to trick users into believing that they must buy or download certain software (that has no real benefit other than for the perpetrator or is malware itself) to address fictitious cybersecurity issues.
It’s also worth noting that scareware is also distributed via spam email that doles out bogus warnings, or makes offers for users to buy worthless/harmful services.
7. Diversion theft

Diversion theft (aka “Corner Game” or “Round the Corner Game”), originated in the East End of London, is the interception of transactions. In an old-school diversion theft scheme, the thief persuades a delivery driver or courier to travel to the wrong location or hand off a parcel to someone other than the intended recipient. In an online diversion theft scheme, a thief steals sensitive data by tricking the victim into sending it to or sharing it with the wrong person. The thief often accomplishes this by spoofing the email address of someone in the victim’s company—an auditing firm or a financial institution, for example.
8. Baiting

Baiting is like the real-world Trojan Horse that uses a false promise to provoke the victims' greed or interest. A baiting attack is built on the premise of someone taking the bait, meaning dangling something you want to entice you to take an action the criminal desires. They set a trap that steals the victims' personal information or inflicts their systems with malware.
Popular methods of baiting can include:
- Physical Baiting: USB drives left in public spaces, like libraries and parking lots making passersby eager to see the contents on the device. Once the user plugs the device into his/her computer, malware is downloaded into the victim's hard drive and hence allowing attackers to have access to the victim's personal information.
- Digital Baiting: Email attachments including details about a free offer, or deceitful free software.
This is a highly effective technique since cybercriminals try to capitalize on your emotions, preying on your desires and impulsivity.
9. Quid pro quo

Quid pro quo means “something for something” in Latin. Just like its name, Quid Pro Quo social engineering attacks are all about give and take between the end users and the hackers, in which the attacker pretends to provide something in exchange for the target's information or assistance. Users are enticed by the promise of money, free travel vouchers, or gifts in exchange for login information or other sensitive details such as social security numbers and bank account numbers. Often, the perpetrator would pretend to be a customer support executive or a technical expert and target unwitting victims, promising them a service in return for confidential data.
10. Contact spamming

One of the earliest methods that is still in use today is contact spamming. If a hacker gains access to your email or social media account, they may send a message to your contacts saying something like, "I've seen this awesome video, check it out!"
Sadly, we have the propensity to put stock in communications seeming to come from those we hold dear. But your device will be compromised if you visit this link. Worse, once these viruses infect your device, they may also infect your contacts with an identical message. (Here, once again, we see how these social attackers use a characteristic of human nature to further their agenda.)
Don't Be a Victim: Preventive Measures
Social engineers manipulate human feelings, such as curiosity or fear, to carry out schemes and draw victims into their traps. Therefore, be wary whenever you feel alarmed by an email, attracted to an offer displayed on a website, or when you come across stray digital media lying about. Being alert can help you protect yourself against most social engineering attacks taking place in the digital realm.
Moreover, the following tips can help improve your vigilance in relation to social engineering hacks.
Self-consciousness - Social engineering attacks are successful because of the casual behavior of humans. The social engineer will always try to build trust. The attacker will show urgency in getting any information from you, in such a case you need to slow down the conversation and check before trusting the person. One should also always be conscious about what they are sharing on social media. For example, if an important website has your security question as your first school name and you’ve already shared it on social media then you're just making the attacker’s job easier. Do not overshare personal information on social media.
Education - Social engineering attacks primarily occur due to employee negligence or lack of awareness. So, raising cybersecurity awareness is the prime solution to improve employee awareness and knowledge about various attack vectors. Cybersecurity awareness can build the strongest defense. If you know what to expect, it will be easier to avoid the trap.
Authentication - Authentication is the basic need of all security systems. The attacks like tailgating, piggybacking, pretexting and quid pro quo result from weak authentication. Double-check the identity of whoever you’re communicating with, especially if it’s an email, text, or call you weren’t expecting.
Think twice - Do not hesitate to doubt! Being doubtful always results in your good. One can avoid the social engineering attacks like phishing, spear-phishing, fishing, and baiting by just giving a second thought before proceeding into a trap. In these doubtful situations, remember to take it slowly. Scammers want you to respond quickly and then think about it afterward. If the communication employs high-pressure sales methods or portrays a feeling of urgency, be suspicious; never allow their haste to affect your careful analysis. Remember that if it sounds too good to be true, it probably is.
Be updated - People are likely to fall for social engineering traps, as some are very hard to detect. In this case, only a good and up-to-date antivirus system can help the victims. Keep your operating systems, antivirus software, and other cybersecurity systems updated with the world. Also, keep updated on your email platform as the spam filter of your email software gets upgraded. Also, be aware of the passwords being used for different websites. Do not use the same passwords for multiple websites. Keep your passwords updated if you feel you’ve been attacked. Changing the passwords regularly always helps.
Use a VPN - Using a reliable VPN, such as SysVPN, can help disguise your identity and prevent would-be hackers from eavesdropping on your communications, even when you're hopping on public Wi-Fi. SysVPN's CyberSec feature will also help to prevent you from visiting malicious websites and cyber threats.




