Cookie Hijacking: The Silent Threat Lurking in Your Browser
Cookies: the unsung heroes or villainous spies of the internet? It's a debate as old as the web itself. While some see cookies as harmless bits of data that make their online experience smoother, others fear the worst - that they're just tools for hackers to steal their private information.
In this today’s article, let's set the record straight once and for all!
Cookies are like secret agents, quietly collecting information about your browsing habits to improve your user experience. They help you stay logged in to your favorite sites, remember your preferences, and even suggest personalized content.
But don't be fooled by their sweet name, the danger lies in what can happen when these cookies fall into the wrong hands. Cybercriminals can hijack your cookies and gain access to your accounts, putting your personal information and sensitive data at risk.
What Are Computer Cookies Exactly?
Before we take a deep dive into the murky world of cookie hijacking, let's make sure we're all on the same page about what cookies actually are. Here, we're not talking about the ones grandma used to bake - we're talking about computer cookies. These little nuggets of information are the unsung heroes of the internet, working tirelessly behind the scenes to enhance your online experience.
You might know them by different names - HTTP cookies, Internet cookies, Web cookies, Computer cookies, or Browser cookies - but they all serve the same purpose. They're like tiny digital assistants, storing information that your web browser saves and sending it back to the website without any changes.
Whenever you visit a website, a cookie is created and stored in your browser. It's like a personalized greeting from the site, helping it remember your preferences, account information, and even the ads you've seen. So, the next time you return, it feels like coming back to an old friend.
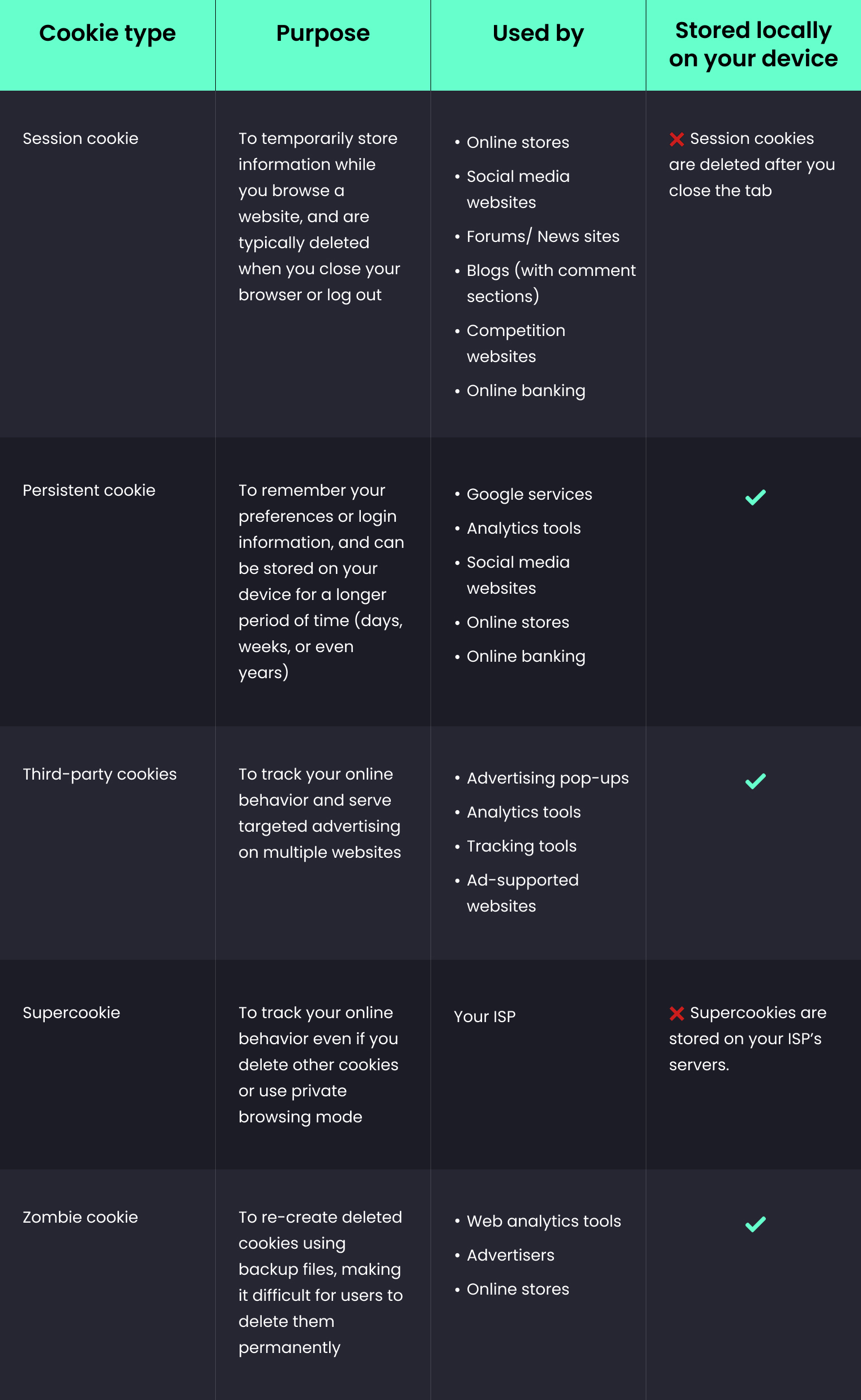
Session cookies
Imagine you're walking into a store and the staff there remembers your name, your preferences, and even your favorite color as soon as you walk in. That's how session cookies work on websites! They remember your information as long as you're browsing the site. But just like how the store staff forgets about you as soon as you leave, session cookies are deleted once you close the website. This is because they contain sensitive information that could pose a risk to your online security. So, these cookies are like little helpers that only work while you're on the website, making your browsing experience smoother and more personalized.
Persistent cookies
Have you ever clicked on "Save" or "Remember Me" when logging into a website? That's how persistent cookies make your online life easier! They remember your settings, preferences, and passwords so you don't have to keep re-entering them.
Unlike session cookies that vanish once you leave a website, persistent cookies stick around even after you close your browser or device. They have an expiration date set by the website, and only then are they deleted. So, you can think of persistent cookies as a helpful friend who stays with you for a while, until it's time to say goodbye. And if you ever need a clean slate, you can always manually delete these cookies.
First-party cookies
Have you ever noticed those little messages that pop up when you visit a website saying something like "We use cookies to improve your experience"? Well, those are first-party cookies and they're like a website's own personal helper.
They store information that helps the website run smoothly, like your language settings and account details. And because they're essential for the website's performance, your browser won't let you disable or delete them. But that's okay because first-party cookies are only accessible to the website owner and aren't shared with advertisers or vendors.
So, just like how a good helper only focuses on one job, first-party cookies only track you while you're on that particular website. Once you leave, they say their goodbyes and wait for your next visit.
Third-party cookies
Imagine you're a book lover who frequently visits Goodreads, follows your favorite authors on Twitter, and reads news on Kindle Unlimited. Third-party cookies are like tiny trackers that follow your activity across all these different websites. This means that advertisers can target you with book ads on various platforms, such as Instagram or YouTube, based on your interests.
Fortunately, some web browsers like Firefox and Chrome allow you to turn off third-party cookies. This can help protect your privacy and prevent targeted ads from appearing everywhere you go online.
Supercookies
Supercookies are like sneaky little spies injected into your internet connection by your internet service provider (ISP). Unlike regular cookies, supercookies are stored remotely and cannot be deleted or blocked by ad blockers or scripts.
This means that your ISP can keep tabs on your online activities, even if you regularly clear your browsing history. It's like having a mini detective sitting between your device and the websites you visit, tracking everything you do.
The scary part is that if someone malicious were to get their hands on your supercookies, they could expose your entire browsing history.
Zombie cookies
Zombie cookies are not your ordinary cookies that you can easily delete from your browser. They are called zombie cookies because they use Adobe® Flash Player vulnerabilities to bring themselves back to life even after you delete them.
What makes zombie cookies different from regular cookies is that they are larger in size and not stored in your browser, but in the Adobe® Flash directory. This makes them harder to detect and delete.
These creepy cookies are like fictional zombies that refuse to die, constantly monitoring your online activities. They follow you around, watching every move you make, just like they're after your brain! Okay, that was a terrible joke, but you get the point. So, it's important to regularly delete cookies to protect your online privacy, but beware of the sneaky zombie cookies lurking out there.
With the amount of data contained in cookies, it’s no wonder cybercrooks want to steal them.
What is cookie hijacking?
Have you ever noticed how some websites seem to know you so well? It's almost like they have a sixth sense about what you want or need. Well, that's thanks to the clever little things called cookies. When you log in to a website, you're essentially opening up a secret conversation with the web server. But how does the server know that it's really you and not an imposter trying to sneak in? That's where cookies come in - they're like a secret handshake that only you and the server know. The server sends a special cookie to your device, which acts as your digital passport for the entire session. So whether you're checking your bank balance, scrolling through Facebook, or shopping on Amazon, the server knows that it's really you behind the screen. And the best part? Cookies make your online experience seamless, so you don't have to keep logging in every time you visit a new page. It's like having your own personal butler who remembers all your preferences and makes your life easier without you even realizing it.
When it comes to cookie hijacking, there are 2 major categories to be aware of, each with its own set of risks and consequences.
The first is known as an active attack, where the perpetrator takes over your session and prevents your device from communicating with the web server. By posing as you, the hacker can perform actions that only you would normally be able to do. This type of attack can be particularly devastating, as the criminal may be able to make unauthorized purchases, change passwords, or even recover accounts as if they were you. The danger of active attacks lies in the fact that they are often difficult to detect and can result in significant financial or reputational damage.
Another type of cookie hijacking to be aware of is known as a passive attack. Unlike active attacks, in which the perpetrator takes over your session and kicks you off the server, passive attacks involve a more stealthy approach. In a passive attack, the criminal quietly observes the data traffic between your device and the server, collecting your sensitive information without raising suspicion. This can include your passwords, credit card details, and other sensitive information that you may not want falling into the wrong hands.
How cookie hijacking happens
Cookie hijacking is a serious threat that can occur through a variety of methods. While many cookie hijacking tactics exploit vulnerabilities in web servers, some attacks can also take advantage of poor security on the user's end.
Brute force attacks
Brute forcing is one of the oldest ways to compromise digital information. It’s quite time-consuming and ineffective. During this attack, the hacker doesn’t actually steal your cookie. Instead, they try every possible combination to guess your session ID and hijack your session.
Malware injections
Malicious software, or malware, can wreak havoc on your device in a variety of ways. It can carry out unauthorized actions, infect your files, and even steal your personal data. But did you know that malware can also be used to perform cookie hijacking and send your sensitive information straight to attackers?
This is just one of the many ways that cyber criminals can exploit vulnerabilities in your online security. Once they gain access to your cookies, they can impersonate you and take over your accounts, steal your identity, and ruin your digital life.
Cross-sites scripting
Cross-site scripting is a technique used by hackers to inject malicious code into legitimate websites or applications, taking advantage of any vulnerabilities present. Once a user visits the compromised website, the code activates, stealing their cookie and transmitting it to the attacker.
IP spoofing
IP spoofing is a technique used by hackers to mask their identity by changing the original IP address of their packet to make it appear as if it came from someone else, such as you. This can be done to gain unauthorized access to a website or server. During the initial three-way TCP handshake, the attacker can intercept the connection with a spoofed IP address, tricking the server into thinking it's communicating with you. This allows the attacker to perform TCP session hijacking and gain access to sensitive information.
Session fixation
Session fixation is a technique used by attackers to fix a session ID they created to your browser. They typically achieve this by sending you a phishing email or message that prompts you to click on a malicious link. This link will then assign a session ID that the attacker can use to access the session as if they were you, thereby hijacking your session.
Protect your online sessions
Here are some steps you can take to safeguard your browsing session.
1. Encrypt your data with a reliable VPN
If you're concerned about the security of your online activities, using encryption is a surefire way to prevent cookie theft. One excellent tool for encryption is a virtual private network (VPN), which provides anonymization and security features. One great example is SysVPN, which works by concealing your IP address and redirecting your traffic through an encrypted tunnel. This additional layer of security and privacy ensures that your online activities remain private and secure, as no one outside of the tunnel can see what you're doing.
2. Avoid unsecure Wi-Fi networks
The problem with public Wi-Fi is that it's open to anyone, including malicious individuals. This creates an easy opportunity for cyber attackers to gain access to your data by using tactics like phishing, malvertising, and malware distribution. It's a scary thought, but it's the reality of the world we live in.
If you find yourself in a situation where you must use an open network, there is a way to protect yourself. The solution is to connect to SysVPN first. This powerful tool hides your IP address and encrypts your connection, keeping you safe on unsecured networks. This means that your data is unreadable to third parties, making it impossible for cybercriminals to steal your cookies or spy on your activities. With SysVPN, you can browse with confidence, knowing that your privacy and security are protected.
3. Don’t click on suspicious links
In today's digital age, it seems that links are everywhere - in emails, private messages, social media posts, and even SMS messages. This constant bombardment of links can make people less cautious about where they click, which is a potentially dangerous habit that needs to be broken.
Behind every link lies a hidden danger, just waiting to invade your privacy, infect your device with malware, and steal your sensitive information. The threats are numerous and come in many forms, from phishing scams to malicious websites designed to look like legitimate ones. But with a little bit of knowledge and a healthy dose of caution, you can protect yourself from these lurking dangers and keep your personal information safe. So next time you come across a link, remember to think twice before clicking.
4. Refrain from insecure websites
It's important to be aware of whether or not a website is using an SSL certificate if you're browsing the internet. Without this added layer of security, your connection to the site is left vulnerable, as the traffic between you and the website is not encrypted.
Luckily, there's an easy way to check if a website is secure. Simply look for a little lock icon next to the website's URL. If the lock is present, it means that the website is using an SSL certificate to encrypt the connection, making it safe to browse. On the other hand, if the lock is missing, it's best to avoid the site altogether, as your personal information and browsing activity may be at risk. Stay vigilant and protect your online safety by checking for that little lock icon.
5. Download software carefully
Downloading apps can be a risky business, especially if you're not careful about where you get them from. To avoid unintentionally infecting your device with malware, it's essential to only download apps that you know to be legitimate. One of the best ways to ensure that the apps you download are safe is to exclusively purchase them from their official stores.



